Introduction
Email is one of the most common vectors for cyber attacks. Phishing attacks are on the rise, and it is essential to know what they are, the most dangerous types and how to protect yourself.
Hackers and cybercriminals are always looking for new ways to exploit users and are getting more sophisticated in their attacks. Email is a favorite vector used to tweak phishing attack techniques and create new types of attacks, such as clone phishing.
Clone phishing is one of the most dangerous types of phishing attacks, and it is on the rise, but there are steps you can take to protect yourself.
This blog post will discuss clone phishing scams, how to detect them, and how to protect yourself and your organization against them.

What is Clone Phishing?
Clone phishing is a type of phishing attack in which a hacker steals the content and recipient email addresses of a legitimate email, creates an almost identical email, and interjects themselves in the middle of an email thread. This can be very dangerous, as recipients may be unable to tell the difference between the two emails: the original legitimate email and the fake one.
What is the Difference Between Phishing and Clone Phishing?
Phishing and clone phishing attacks leverage fake emails that hackers and cybercriminals use to steal information or trick users into downloading malicious codes.
Phishing is the more common of the two, and it involves sending an email to a victim that looks like it is from a legitimate source. The goal of the email is to get the victim to click on a malicious link, install malware, or provide sensitive information.
Clone phishing is very similar to phishing, but it involves stealing the content and recipient addresses of a legitimate email and using them to create an almost identical email. Malicious threat actors can easily exploit this to their advantage, as people often cannot tell the difference between fake and real emails.
How Clone Phishing Works?
In a clone phishing attempt or a clone phishing scam, a cyber attacker will first compromise a user’s email account, then watch and monitor email traffic between the user and trusted parties. The attacker will, at some point, intercept legitimate threads to inject themselves in and start receiving emails from a business, for instance.
The attacker will then replaces any legitimate document attachments with malicious ones when the reply is sent back. If employees within the target organization can’t detect these malicious attachments or cloned emails, they may be tricked into downloading malware onto their computers.
Although clone phishing typically uses email message replies, it can also be done by copying a legitimate email, usually sent from a known business to a targeted recipient. This malicious copy may contain malware attachments such as rootkits or ransomware, among other malware.
Though the initial message may differ, clone phishing is usually successful because recipients get a response to a real email instead of a new message in an average phishing attack. Also, email filters are more likely to let in a harmful reply since it’s sent from someone legitimate using approved channels.

The Risks of Clone Phishing
Clone phishing presents severe risks to individuals and organizations alike, as it can quickly go undetected and result in devastating consequences. Among the risks associated with clone phishing are financial risk, identity theft, system compromise, brand and reputation damage, human capital, and business disruption.
- Financial risk: Clone phishing can result in significant financial losses as criminals scam individuals and organizations out of their money.
- Identity theft: Clone phishing targets personal and confidential information such as passwords, login credentials, banking details, and credit card numbers. Criminals can then use this information to steal identities or commit other crimes.
- System compromise: Clone phishing can be used to install malicious software on systems, which can then be used for various purposes, such as spying or data theft.
- Brand and reputation damage: Clone phishing is often associated with scams or other illicit activities that can tarnish the reputation of organizations or individuals targeted by these phishing emails.
- Business disruption: Clone phishing can significantly disrupt organizations’ daily operations and business activities, as they may have to deal with compromised systems, stolen data, financial losses, or other negative consequences.
Clone Phishing Examples
Messages in a clone phishing attack can vary, but they often share some common features. These messages usually contain language that makes them seem urgent and may have malicious links or attachments.
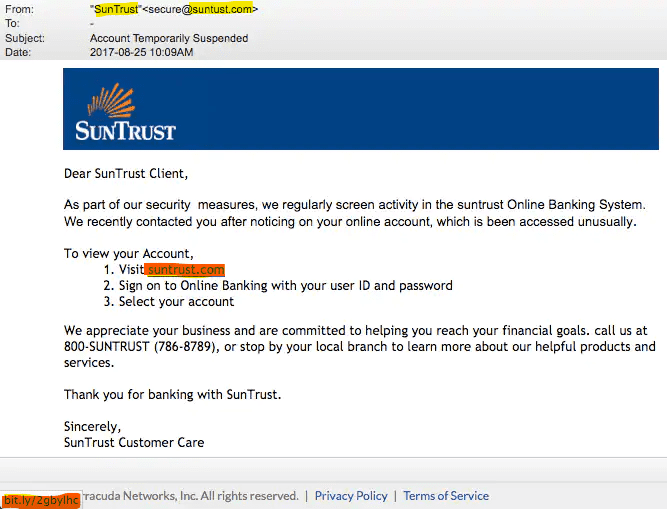
Below is an example of clone phishing with a sender’s email address that is not legitimate and a display link that is different from the actual destination link.
How to Detect Clone Phishing Attacks?
Clone phishing attacks are challenging to detect because they often look like legitimate emails. However, there are some things you can look for to help detect these attacks.
One thing to watch out for is the sender’s email address. Clone phishing emails will often have a different address than the real email. Check the address carefully before clicking on any links or opening any attachments.
Another thing to watch out for is mismatched fonts or graphics. Clone phishing emails may not have the same fonts or graphics as the real email, so be on the lookout for differences.
You can also check the link destination before clicking on any links. Most browsers will show you the link’s web address when you hover over it with your mouse. If the address doesn’t match the website it’s supposed to go to, then it’s probably a clone phishing attack.
Finally, pay attention to the sender’s tone and language. Clone phishing emails often use aggressive and urgent language in an attempt to prompt you to take action right away.
You can detect clone phishing attacks by staying alert and paying attention to these red flags.
Must Read:

How to Protect Against Clone Phishing Attacks?
You can take a few proactive steps to ensure you aren’t caught in a clone phishing scheme.
- User Awareness and training: End users have the potential to be the first and last line of defense against clone phishing. With knowledge of what to look for, they can be well-equipped to spot clone phishing emails.
- Anti-spam software: You can avoid clone phishing effortlessly using this technology. It will eliminate any emails that look suspicious without anyone having to put in any extra effort.
- Anti-malware software: Likewise, clone phishing emails can be blocked before they even make it to your inbox with the help of anti-malware software. This powerful tool will scan incoming emails for any signs of malicious activity and act accordingly.
- Password managers: A password manager is a great way to ensure that clone phishing attackers don’t gain access to your accounts. With the ability to automatically fill out login forms, clone phishing attacks won’t be able to trick you into handing over your credentials.
- Proxy or next-generation firewall solution: This solution will automatically look for indicators of clone phishing, such as mismatched URLs with bad reputations, so you don’t have to.
- Engage the sender: My favorite way to prevent phishing attempts is by calling the sender and asking whether the email is legitimate. By doing this, you will also alert other legitimate parties.
What to Do if You Receive Clone Phishing Emails?
Do not click on any links or attachments if you receive a clone phishing email! Instead, report the email to the organization it claims to be from and delete it immediately. Alternatively, if the suspicious email is sent to your work email account, forward it to your cybersecurity or IT team.
Conclusion
Clone phishing attacks are a serious threat to businesses and individuals alike. They can be challenging to detect, but there are some red flags you can look for to identify these attacks. Businesses, or yourselves, can also take proactive steps to ensure that clone phishing emails don’t get through to your inbox. If you receive a clone phishing email, don’t click on any links or attachments- report it!